Intelligent Threat Management (ITM) Services
Intelligent Threat Management Team has mastered assorted Security related skills such as assessing the Web, Mobile, Web Services and Networks for their security and reporting the identified vulnerabilities with information in detail. Our Security Certified Professionals are the career hackers and the skills they thrived are not only in assessing the applications for security but also imbibed the in-depth penetration testing approach by exploitation.
The following are the key Security Services Oversoul offers.
-
Web Application Security Testing (DAST)
-
Network & Infrastructure Security Testing (Network VAPT)
-
Mobile Application Security Testing (MAST)
-
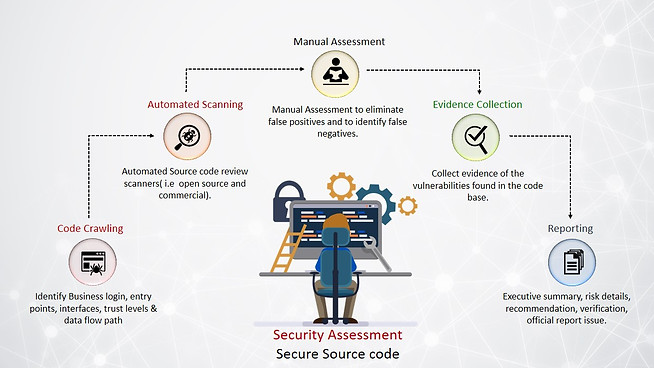
Secure Source Code Review (SAST)
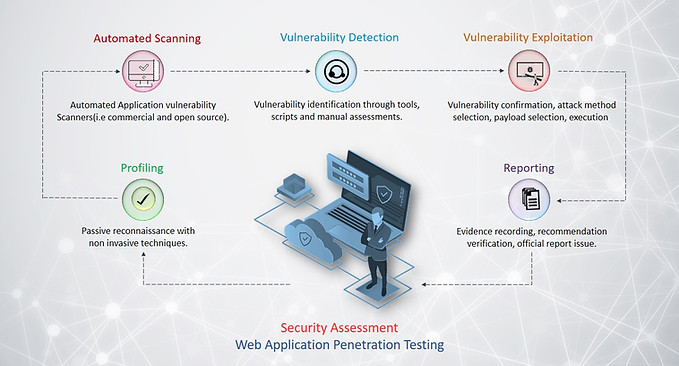
Web Application Security Testing or Dynamic Application Security Testing
Our Security professionals are proficient in identifying the security threats and help in enhancing the security posture of your Web Applications by following the standards set by SANS, OWASP, WASC, etc. Our Team is also accountable in providing the post assessment support such as advocating the solutions to fix the identified vulnerabilities and also providing remediation on need basis.
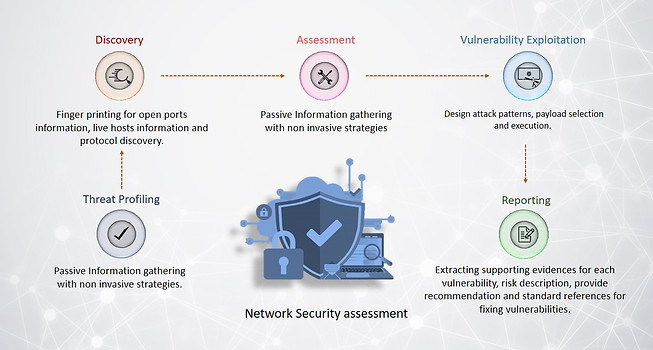
Network & Infrastructure Security Testing (Network VAPT)
The Vulnerabilities in the Network of any organization may lead to the severe vandalization if exploited by the hackers. Our Security experts can be obliging in identifying the Network and infrastructure level vulnerabilities by executing the security assessments before your organizations confront the Network Intrusions or any malicious activities.
Mobile Application Security Testing (MAST)
Oversoul performs customized attacks based on the nature of your mobile applications in both Android and iOS platforms.
Our Smart Security team is dexterous in assessing the mobile applications using the OWASP Top 10 as Mobile Security Bible.
Our team performs security scanning on all credible use cases of mobile application and entire mobile to discover vulnerabilities that may expose sensitive information to the malicious users.